
Open Key Access Protocol
Lightweight protocol for secure, user-controlled AI API key delegation
The Problem
Today
Every app asks you to paste your API key. Keys end up scattered across dozens of apps with no visibility or control.
With OKAP
Your keys stay in one vault. Apps request scoped tokens. Revoke any app instantly without rotating your key.
Architecture
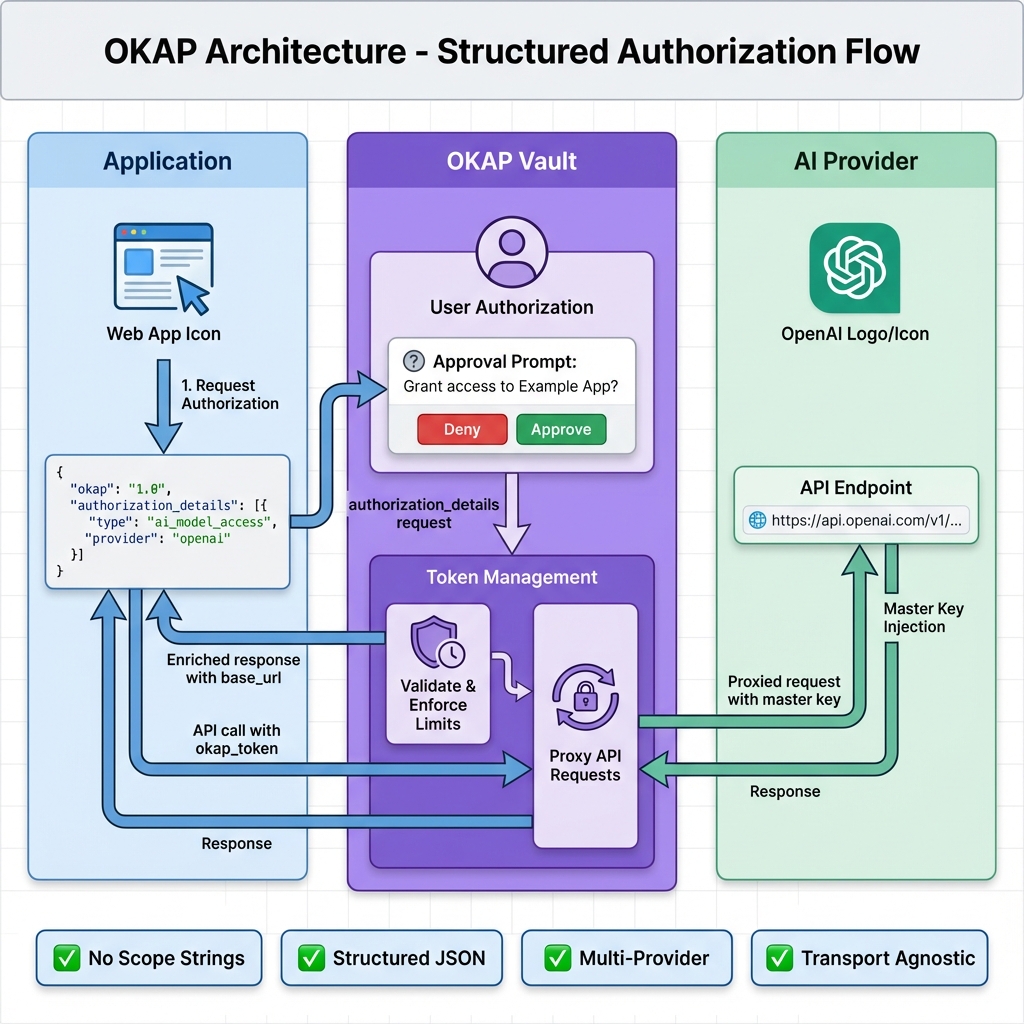
Structured authorization flow using RAR-inspired patterns
Code Example
# App requests access from user's vault from okap import OkapClient client = OkapClient("https://vault.okap.dev") token = client.request_access(provider="openai", models=["gpt-4"]) # Use with OpenAI SDK - key never leaves the vault ai = OpenAI(api_key=token.key, base_url=token.base_url)
The Specification
Structured Authorization
Uses typed JSON objects, not scope strings. Inspired by RFC 9396.
API Proxying
Vault proxies requests, injecting keys and enforcing limits.
Multi-Provider
Request access to multiple AI providers in single authorization.
Get Started
FAQ
Do apps need to support OKAP?
Yes. Apps implement the OKAP client instead of asking for raw keys. The more apps adopt it, the more useful it becomes.
Can I use this with Cursor, Claude Desktop, etc?
Not yet. Those apps would need to add OKAP support. We're building the protocol so they can adopt it.
What providers are supported?
OpenAI, Anthropic, and Google. The protocol is provider-agnostic, so adding more is straightforward.
How are keys stored?
Keys are stored in Cloudflare KV (encrypted at rest), accessed only via authenticated sessions. They're never logged or exposed in responses.
Is the vault a security risk?
Your keys stay encrypted. Apps only receive scoped tokens-never your actual keys. You can set spend limits and revoke any app's access instantly.
Will OKAP get rate-limited as more users join?
No. Each user's requests use their own API key. Rate limits apply to your key, not OKAP.
What if the vault goes down?
The vault runs on Cloudflare's global edge network with automatic failover. Apps with valid tokens continue working. New token requests would fail until restored.
How does this compare to other solutions?
| OKAP | .env files | Secrets Managers | |
|---|---|---|---|
| Scoped access | ✓ | ✗ | ✗ |
| Per-app revocation | ✓ | ✗ | ✗ |
| Spend limits | ✓ | ✗ | ✗ |
| No infra needed | ✓ | ✓ | ✗ |
| AI-provider aware | ✓ | ✗ | ✗ |
Why not just use OpenRouter?
OpenRouter is great! But it's a different model. With OpenRouter, you use their unified key-they manage provider access. With OKAP, you keep your own keys (for enterprise contracts, credits, or full control) and delegate scoped access to apps.
Can I self-host?
Yes, for teams/orgs who want their own infrastructure. Deploy the reference server or Cloudflare Worker to a public URL.